Many times I came across one issue… how to grant access to CLI (Command Line Interface) on Cisco devices without creating separate username and password for each user on each device? In order to resolve that I did use AAA features of Cisco IOS and built-in Windows Server 2008 R2 component – NPS (Network Policy Server).
Those two mixed together can create very nice environment which allows flexible management who, when and how can access network devices. Same time, Active Directory will be central place to grant or deny access to devices as well as enforce specific privilege level.
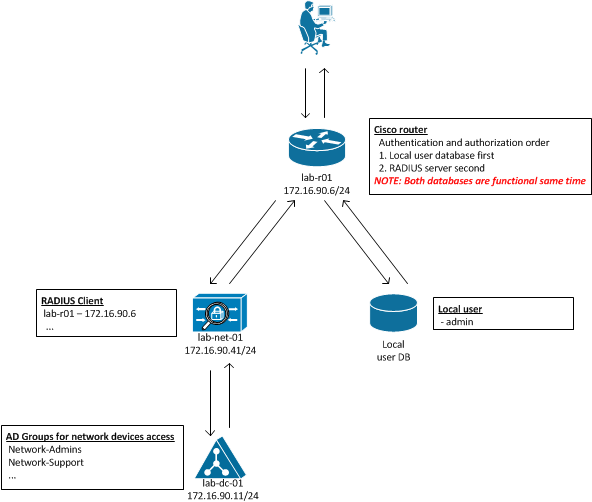
Below is simple diagram of the whole process and steps which take place when accessing Cisco device integrated with NPS/RADIUS.
What happenes when accesing router integrated with RADIUS:
- Operation initiates SSH or Telnet connection to device and enters credentials (username/password)
- Cisco router checks local database for username and password
- Once credentials found in local database operator has access to command line on router
- If credentials not present in local database then request for authentication and authorization is forwarded to RADIUS
- RADIUS checks credentials and group membership with Domain Controller
- If user is member of Network-Admins or Network-Support group access to CLI is granted and Operator can access router, otherwise Operator can’t access Cisco router
Let’s see how to configure whole solution step-by-step…
Objective
NPS integration with Cisco will deliver solution which will allow to authenticate and authorize access to Cisco devices Command Line Interface (CLI) with Active Directory credentials. In addition to that, privilege level will be detemined and enforced based on Active Directory group membership.
Actions which will be taken:
- Appropriate groups will be created in Active Directory
- Network-Admins – for users which will have privilege 15 access to Cisco devices
- Network-Support – for users which will have privilege 1 access to Cisco devices
- Microsoft NPS Role will be added to Windows Server 2008 R2
- Network Policies will be created on NPS/RADIUS
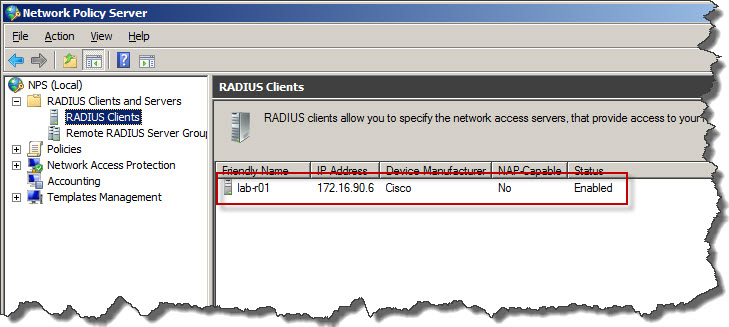
- Cisco router will be added to NPS/RADIUS as client
- Appropriate configuration will be applied to Cisco router
Microsoft NPS Server Role Installation
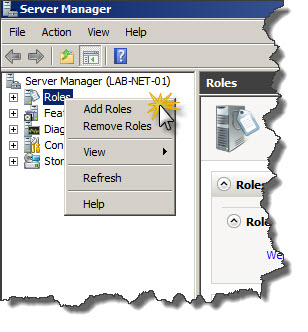
First step is to install NPS on Windows Server 2008 R2. in order to do that Server Manager has to be used. In Server Manager right-clik on Roles and choose Add Roles from context menu.
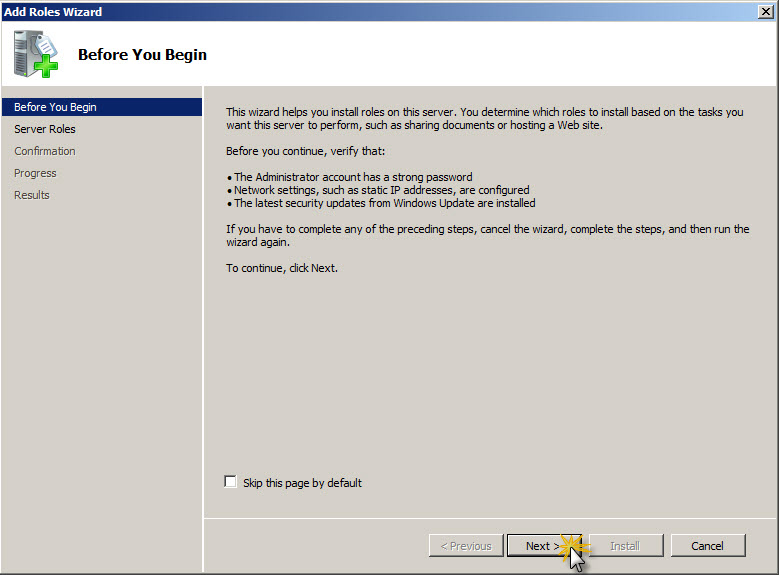
On Before You Begin screen click Next to proceed to Role selection screen.
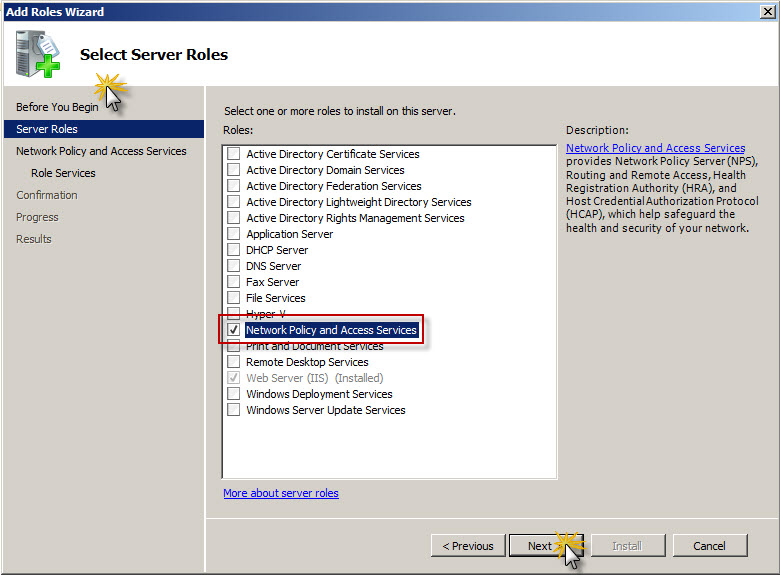
On Roles list locate Network Policy and Access Services, make sure that checkbox on the left side of that role is checked and click Next to proceed to next installation screen.
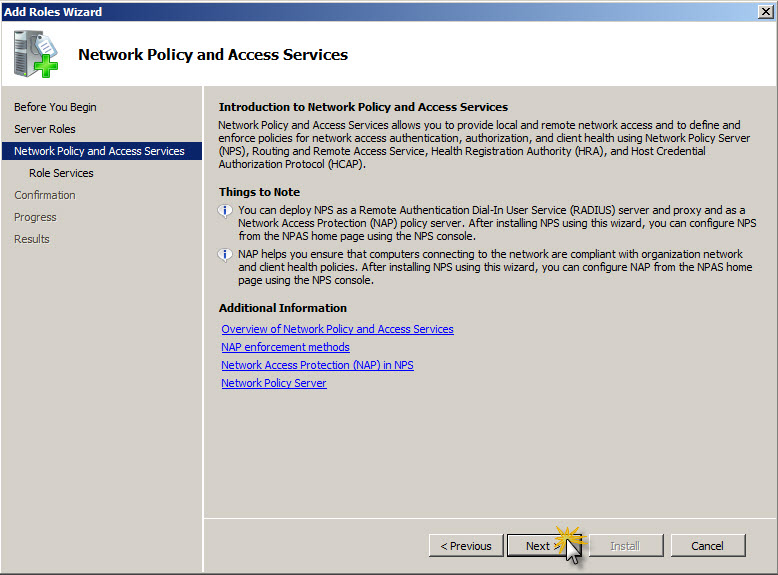
Next screen is Introduction to Network Policy and Access Services. Click Next to proceed to Role Services selection screen.
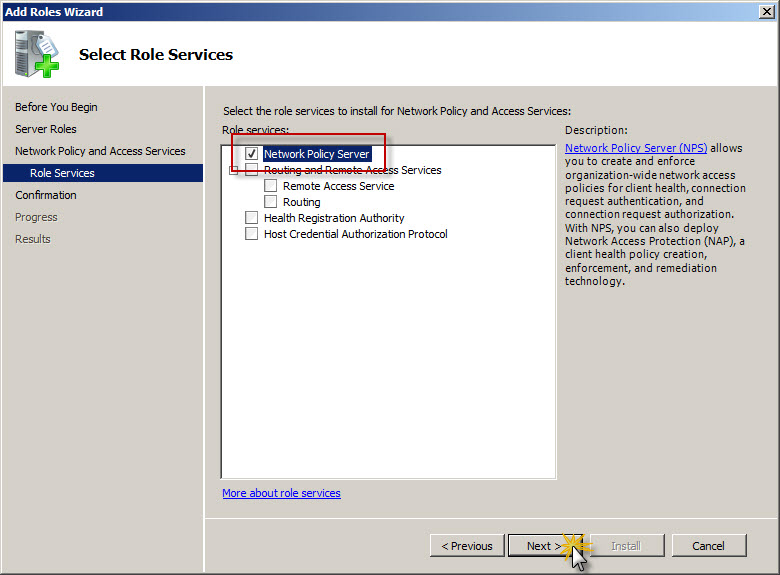
On Select Role Service screen make sure that Network Policy Server checkbox is checked and click Next to proceed to installation summary screen.
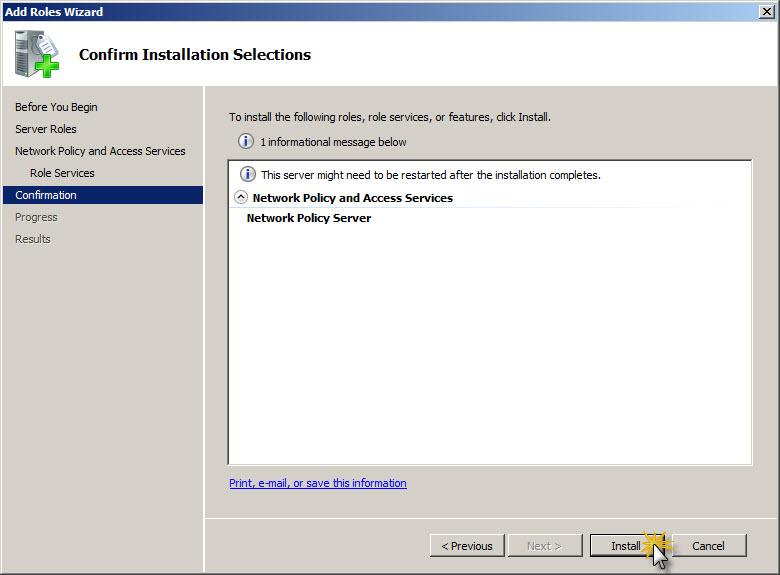
On Confirm Installation Selections screen review if Network Policy Server is shown on the list of services for installation and if everythign is correct click Install to proceed with installation and add new Role to system.
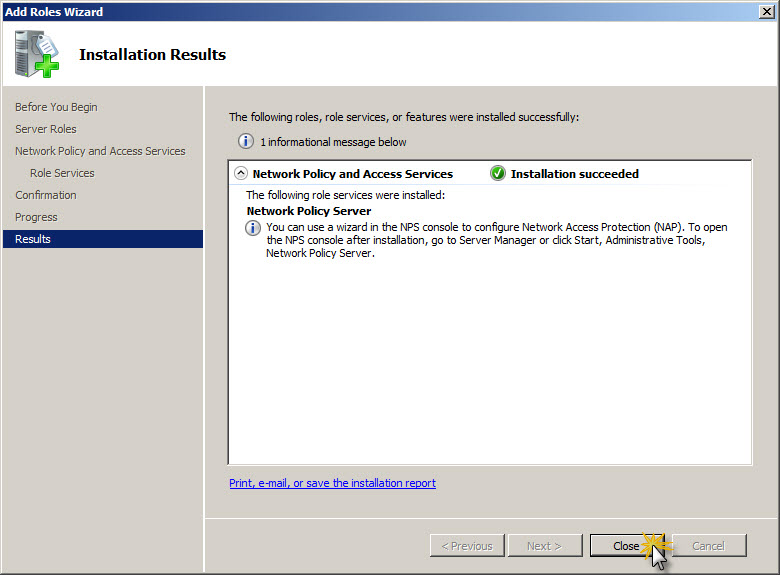
Once all components for new role are installed in the system you will see Installation Results screen where you can find indication if whole process went well ot some errors occured. Once everything went well click Close button.
Now you can go to Start / Administrative Tools and find Network Policy Server icon which has been recently added to system as the effect of new role isntallation. Click that to start NPS management console.
Once you will start NPS management console you can see that one of the components of NPS is RADIUS. This is service we will need and use to provide authentication and authorization to Cisco devices basec on Active Directory credentials and group membership.
Register NPS in Active Directory
First we have to register Network Policy Server in Active Directory to allow authentication based on user accounts we created in domain.
To authorize NPS in AD:
- Logon to server with NPS using account with domain admin credentials.
- Go to Start / Administrative Tools and then click Network Policy Server.
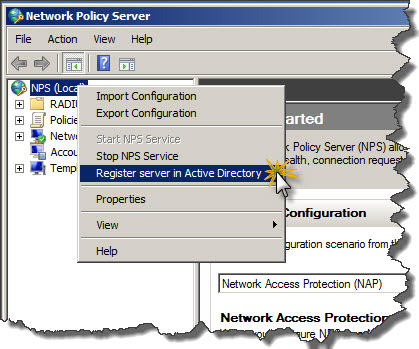
- Right-click on NPS (Local) and from context menu click Register server in Active Directory.
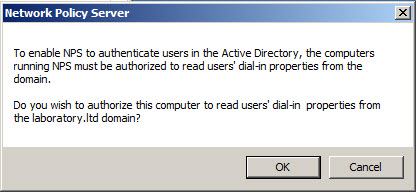
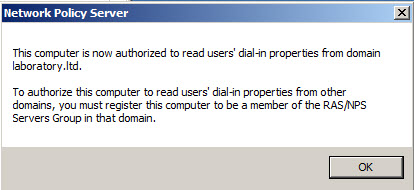
- Confirm that you want to authorize this computer (server with NPS) to access users’ dial-in properties by clicking OK in Network Policy Server dialog window. Make sure that authorization will happen in correct domain as per indication in message from system.
- When operation will be completed with success notification confirmation iwll show on the screen that this computer is now authorized to read users’ dial-in properties from domain.
For everyone who likes to reconfigure servers from Command Prompt here is how to add NPS to default AD domain:
- Log on to the NPS server using account with domain admin credentials.
- Open Command Prompt.
- In CMD window type: netsh ras add registeredserver
- Then press ENTER.
Add Cisco router as RADIUS client
Now it’s time to inform NPS/RADIUS about our router and establish shared secred as form of identification when router will be requesting authentication and authorization from RADIUS and Active Directory.
To add router as RADIUS client:
- Logon to server with NPS using account with admin credentials.
- Go to Start / Administrative Tools and then click Network Policy Server.
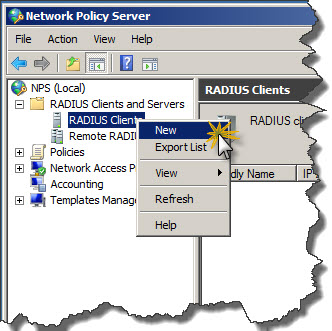
- Expand RADIUS Client and Servers.
- Right-click on RADIUS Clients and click New from context menu.
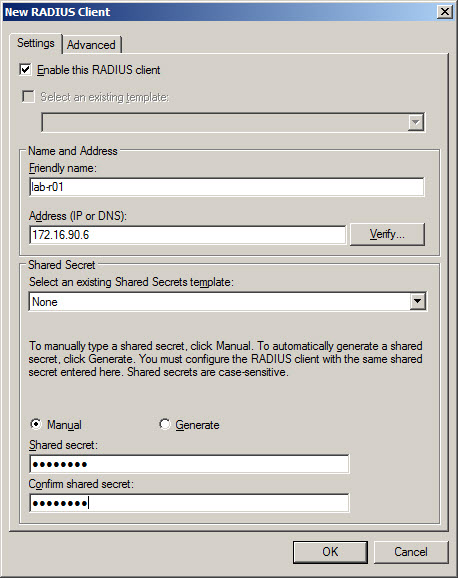
- In New RADIUS Client window Settings tab enter:
- Friendly name of the router – name to recognize router, usually same as hostname.
- Address (IP and DNS) – IP address of the router or hostname – if hostname used proper hostname needs to be registered in DNS prior to RADIUS configuration.
- Shared secret – passphrase which was configured on router which will allow to identify router when requesting AAA from RADIUS.
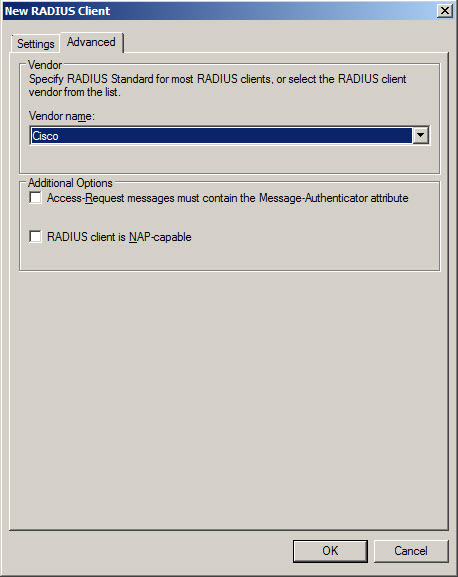
- In New RADIUS Client window Advanced tab enter:
- Vendor name – Cisco – as in this example Cisco router will communicate with RADIUS.
- Once confirmed with OK we will see that router has been added to RADIUS configuration as client.
Adding new NPS Policy for Network Admins
Now it’s time to create Network Policies, which will allow users to access certain devices and enforce particular privilege level on Cisco device.
To add Networ Policy:
- Logon to server with NPS using account with admin credentials.
- Go to Start / Administrative Tools and then click Network Policy Server.
- Expand Policies.
- Right-click on network Policies and click New from context menu.
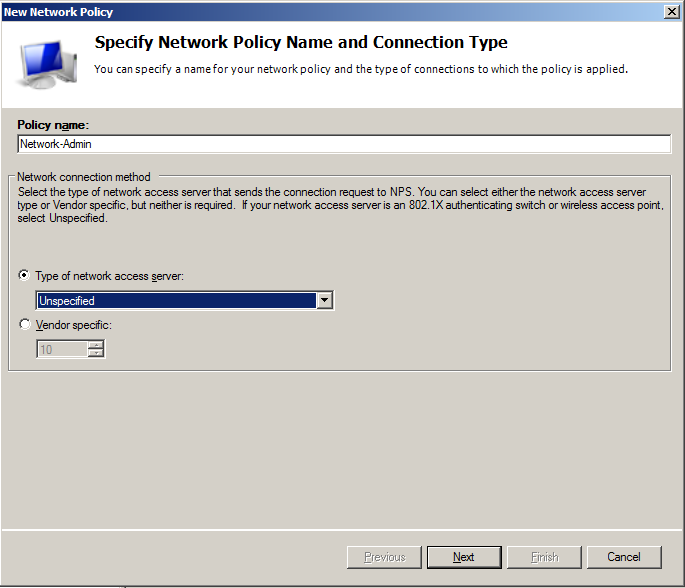
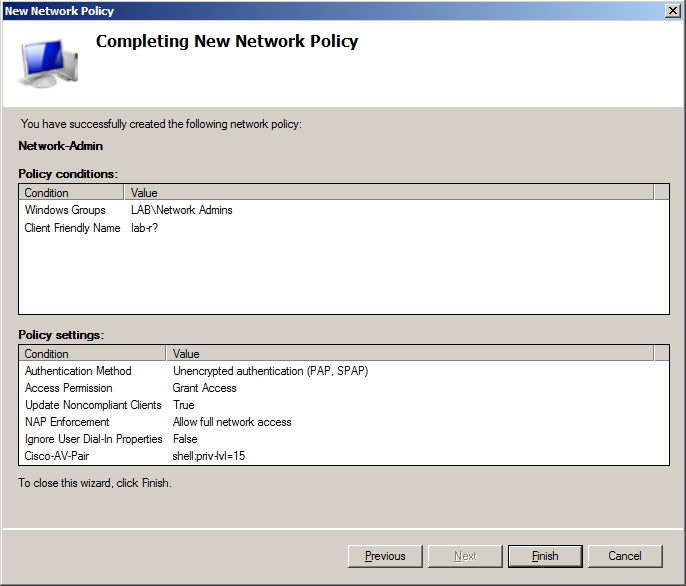
- On Specify Network Policy Name and Connection Type dialog specify policy name, which in that case is Network-Admin and leave Type of network access server as Unspecified.
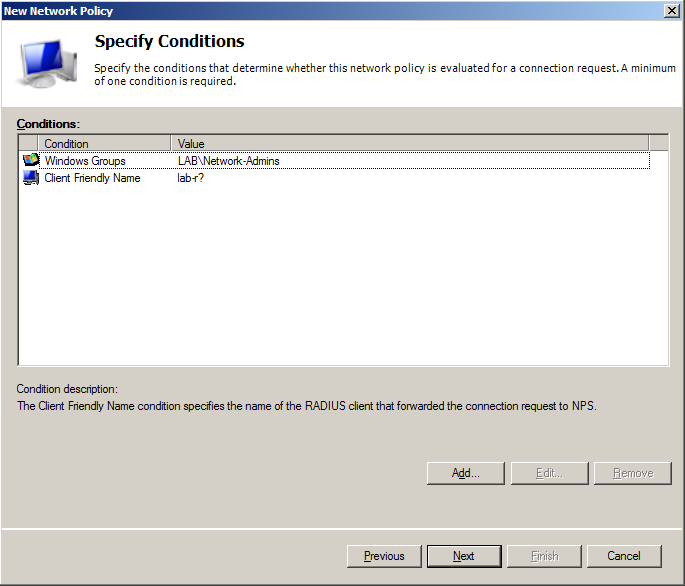
- On Specify Conditionsscreen add 2 parameters:
- Windows Groups – and specify Network-Admins group from Active Directory
- Client Friendly Name – and specify name of device(s) from which operator will have access (in that example router has name lab-r01, so I’m adding lab-r? as Client Friendly Name, which means all devices which have name starting with lab-r, question mark in client name means any string of characters)
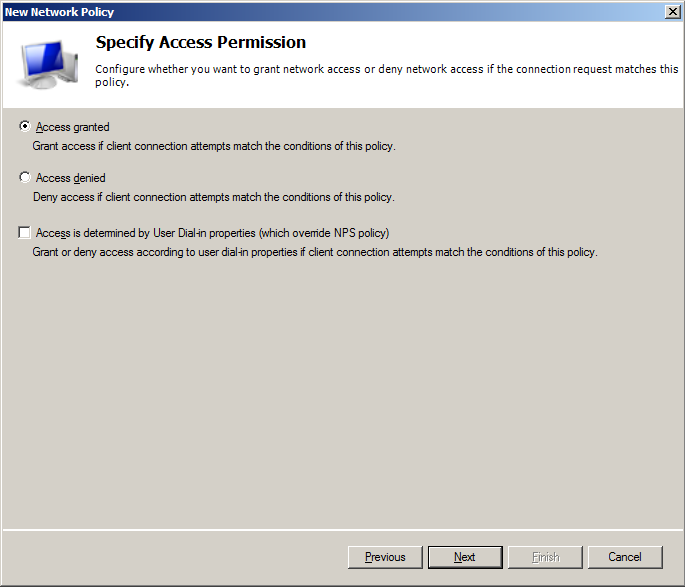
- On Specify Access Permissions make sure that Access granted option ich clicked and Access is determined by User Dial-in properties checkbox is cleared.
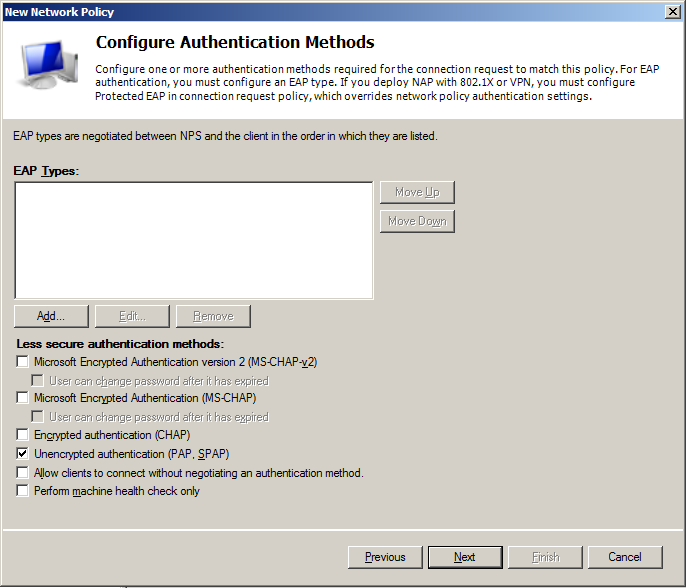
- On Configure Authentication Methods make sure that Unencrypted authentication (PAP, SPAP) checkbox is checked.
- On Configure Contraints screen no changes, so click Next to move on to next step
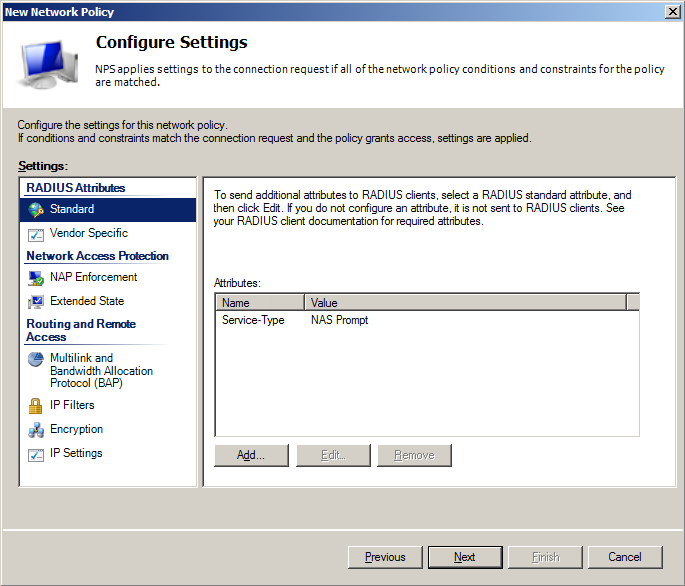
- On Configure Settings screen in Standard section add Service-Type parameter with value NAS Prompt
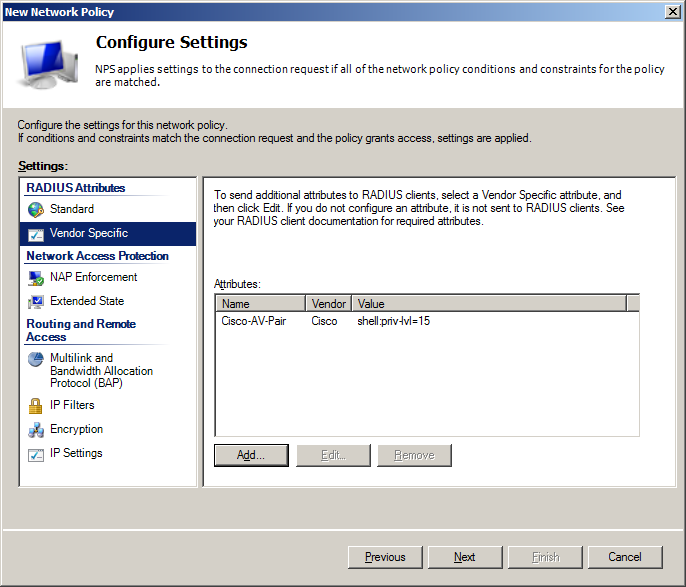
- On Configure Settings screen in Vendor Specific section add Cisco-AV-Pairparameter with value:
- shell:priv-lvl=15 – for Network-Admins policy which will enforce privilege level 15
- shell:priv-lvl=1 – for Network-Support policy which will enforce privilege level 1
- On Completing New Network Policy screen review summary and click Finish to create network policy
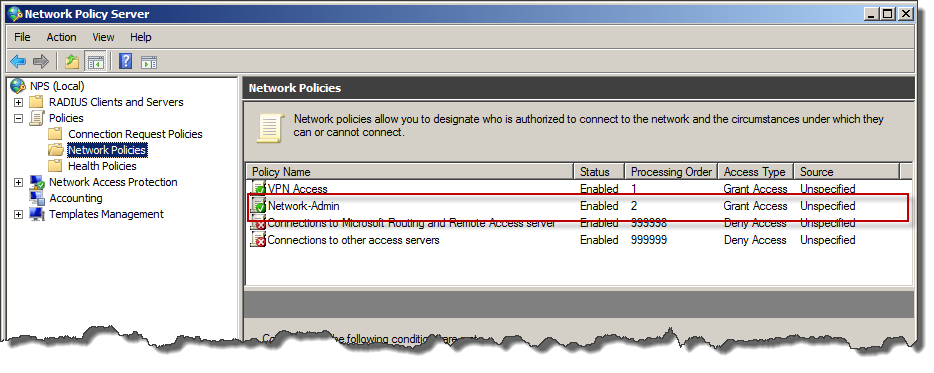
Below created policy on Network Policies list.
Repeat steps in Adding new NPS Policy for Network Admins section to setup policy for each privilege level you want to enforce on Cisco devices.
Define appropriate parameters on Configure Settings screen in Vendor Specific section using Cisco-AV-Pair parameter with value:
- shell:priv-lvl=15 – for Network-Admins policy which will enforce privilege level 15
- shell:priv-lvl=1 – for Network-Support policy which will enforce privilege level 1
Of course shell:priv-lvl might contain numbers between 1 and 15.
Configuration on Cisco IOS
It is time to inform our router or switch that all attempts to access device via telnet or ssh should be authenticated and authorized in local database and if username or password doesn’t match then go to RADIUS.
|
01
02
03
04
05
06
07
08
09
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
|
aaa new-model!aaa group server radius IAS server 172.16.90.41 auth-port 1812 acct-port 1813!aaa authentication login userAuthentication local group IASaaa authorization exec userAuthorization local group IAS if-authenticatedaaa authorization network userAuthorization local group IASaaa accounting exec default start-stop group IASaaa accounting system default start-stop group IAS!aaa session-id commonradius-server host 172.16.90.41 auth-port 1645 acct-port 1646 key secret12keyradius-server host 172.16.90.41 auth-port 1812 acct-port 1813 key secret12key!privilege exec level 1 show config!ip radius source-interface fa0/1!line vty 0 4 authorization exec userAuthorization login authentication userAuthentication transport input ssh telnet!line vty 5 15 authorization exec userAuthorization login authentication userAuthentication transport input ssh telnet |
Test if implementation was successful
For testing purposes I setup 2 users i LAB domain:
- akim – member of Network-Support group
- apearson – member of Network-Admins group
- apeters – member none of network admin or support groups
Network-Support member is accessing device
When member of Network-Support group will access deivce privilege level 1 is enforces and according to configuration with that privilege level user can display configu on the screen.
|
01
02
03
04
05
06
07
08
09
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
|
C:\>telnet 172.16.90.6User Access VerificationUsername: akimPassword:lab-r01>sh confUsing 1769 out of 57336 bytes!version 12.4service timestamps debug datetime msecservice timestamps log datetime msecno service password-encryption!hostname lab-r01!boot-start-markerboot-end-marker!enable secret 5 $1$U7IF$U8hEIH38g7KWwf9Sc8tt.1!aaa new-model!!aaa group server radius IASserver 172.16.90.41 auth-port 1812 acct-port 1813!aaa authentication login UserAuthentication local group IASaaa authorization exec UserAuthorization local group IASaaa authorization network UserAuthorization local group IASaaa accounting exec default start-stop group IASaaa accounting system default start-stop group IAS!lab-r01> |
Network-Admins member is accessing device
When member of Network-Admins group will login to device automatically privilege level 15 is enforced, so full access to device is granted.
|
01
02
03
04
05
06
07
08
09
10
11
|
C:\>telnet 172.16.90.6User Access VerificationUsername: apearsonPassword:lab-r01#conf tEnter configuration commands, one per line. End with CNTL/Z.lab-r01(config)# |
Member none of the network admin or support groups is accessing device
When user is not a member of any of authorized groups (neither Network-Admins nor Network-Support) access to device is refused.
|
01
02
03
04
05
06
07
08
09
10
11
|
C:\>telnet 172.16.90.6User Access VerificationUsername: apetersPassword:% Authentication failedUsername: |
Enjoy ![]()
I was going to write theis how to up but SKufel over at did such a winderful job I am reposting his documentation his link is https://blog.skufel.net/2012/06/how-to-integrating-cisco-devices-access-with-microsoft-npsradius/